In 2016, Hollywood Presbyterian Medical Center, a Los Angeles Hospital, fell victim to ransomware. Hackers encrypted patient records, x-rays, and other life-saving patient data. They requested $3.6 million in bitcoin to release the data. At the time of the attack, medical staff resorted to taking notes about their patients by hand.
Not all ransomware attacks are potentially life-threatening like these but it is hard, if not impossible, to be productive if your site is taken over by hackers. The following are some tactics that you can employ to protect your WordPress site from this insidious form of malware.
What Is Ransomware?
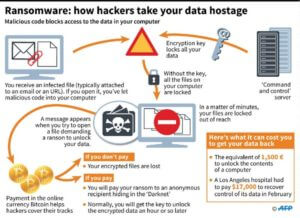
Ransomware is an ugly form of software that hackers install on your computer or your server. They do this by exploiting vulnerabilities in your system. The installed software can either sit in the background and run quietly before it is activated or it can activate immediately.
Once activated, you will have the unnerving experience of watching all of your files be locked one by one in front of your eyes. There’s nothing you can do about it. You’ll no longer have access to your WordPress e-commerce site customers’ orders or product data. In fact, any data you work with on a daily basis is locked up behind a hacker’s bad intentions and you don’t have the key.
Hackers will gladly decrypt your information as long as you are willing to pay them. Sadly, most victims have no choice but to do this, which is often requested in Bitcoin as it gives them an anonymous way to receive their booty. Unfortunately, many victims find out after paying the ransom that the hackers had no intention to decrypt the hostage data.
Protect Your WordPress Site from Ransomware
Realistically, there is no way to 100 percent protect your site from ransomware. This is because hackers are constantly evolving and creating new tricks and techniques designed to exploit unknown vulnerabilities. The goal is to minimize your risk and take necessary measures to protect yourself in worst-case scenarios. Here are a few tips to help protect your WordPress website.
1. Keep Your Content Management System Up-to-Date
Every day, new WordPress attacks are developed. WordPress responds by issuing security patches. You need to have the latest security patch implemented to keep your site safe. This process is comparable to keeping your OS for your PC or your Mac up-to-date.
The same is true for themes and plug-ins. Most developers do a good job at implementing updates and releasing them frequently. You should update your host PHP and MySQL versions as well.
2. Protect against Brute Force Attacks
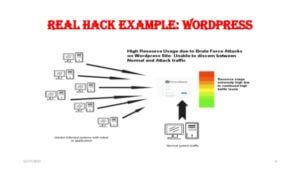
The easiest way to protect your WordPress site against brute force attacks is to ban IP addresses that try to access your site multiple times with incorrect login details. Without this, hackers are able to bombard your site with hundreds of passwords and username combinations every single minute until they find the right one and are able to break in.
3. Change the WordPress Database Prefix
WordPress has a default database prefix. Using this makes your site susceptible to SQL injection attacks. You can prevent these attacks by simply changing the default ‘WP’ – to a unique term that you select. For example, it could be ‘John16WP’.
But what if you start a blog and installed WordPress on your website using the default prefix? There are a ton of plug-ins that you can download that will allow you to change it. Just as a word of caution, make sure that you backup your site before you do anything on the database.
4. Turn off File Editing
If criminals are able to gain admin access to your WordPress dashboard, they have the power to edit the files that make up your WordPress installation. This includes editing plug-ins and themes. Protect yourself by disabling file editing. This way, even if hackers takeover your WordPress dashboard, they will be unable to modify your files.
Do this by adding define (‘DISALLOW_FILE_EDIT’, true); to the very end of your wp-config.php file.
5. Backup Everything
We cannot emphasize this enough. Backup everything and backup often. Having more backup points means that you have more of your data saved. One option is to backup your data on the server. The risk is that ransomware may also encrypt your backups if left on your local drive. You can eliminate this issue by creating off-site backups that are stored in a separate location.
What If You Become a Victim?
Do not pay the ransom. This might sound crazy, but as we mentioned at the outset, cyber criminals are adept at encrypting your files, but they do not necessarily know how to decrypt your files, so you may find yourself paying money for nothing. Even if they do give you a decryption key, you will likely need a PHP developer who has experience to fix the code and get your site working again.
One protective measure gaining in recent popularity is a virtual private network or VPN. VPNs encrypt your internet connection, hide your IP address, allow you to surf the web anonymously, and make it difficult for hackers to attack you.
The Future of Ransomware
CNNMoney issued a report that said, according to the FBI, the cost of ransomware has reached an all-time high. Back in 2016, cyber criminals were able to collect more than $209 million in the first three months of the year. Things have not gotten any better.
Many cyber criminal groups operate out of former Soviet republics and in parts of Eastern Europe. Weak law enforcement coupled with reluctance by their governments to cooperate with Western nations makes it difficult to catch these criminals. Couple that with the fact that the ransom is being paid using Bitcoin and it is clear to see why this criminal enterprise is so successful.
Our parting advice is: use your brain! No matter how much protection you have on your website, if you do things like use the word “password” as your password, you’re asking for trouble. Protect yourself and minimize your chance of becoming a ransomware victim.